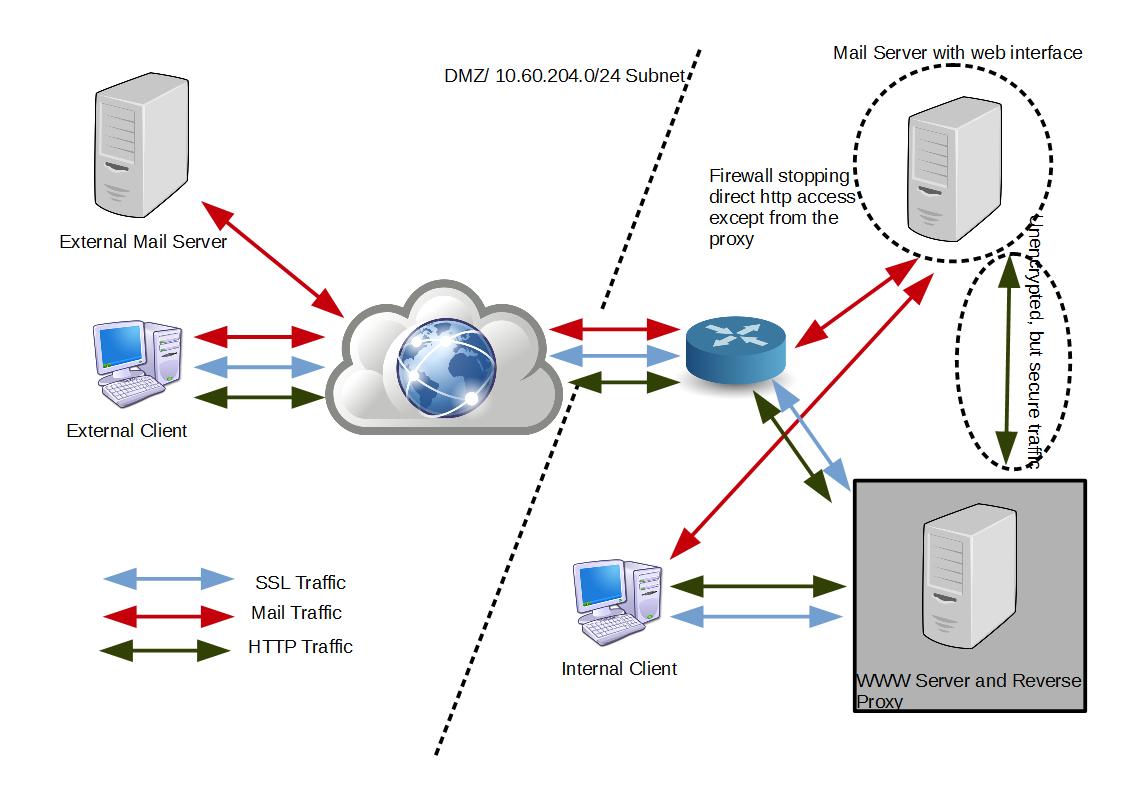
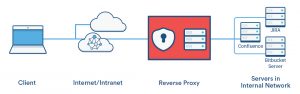
As discussed in earlier posts I have hit the limits of what you might call ‘standard’ hosting. As I have multiple machines, both physical and virtual and only a single externally accessible IP address I needed to figure out how to allow access to certain URLs and applications on these machines without relying on NAT and port forwarding rules at the router (layer 3 routing). I also needed to do this securely using SSL.
This blog entry will outline that process that I followed to modify a significant number of applications to allow access through a single apache host that handled all incoming requests, and secures them with SSL to the client.
As my mail server already had SSL configured it needed to be disabled and go back to only accepting traffic on port 80. As all incoming traffic will be from the reverse proxy and a firewall will block all other requests, this will be secure.
Begin by creating a backup of the VM of the mail server. Then on the mail server (once running again):
Disable the SSL site:
sudo a2dissite default-ssl.conf
Disable SSL forwarding in the .htaccess file in /var/www/html/ such that the file will now look like:
#RewriteEngine On
# Redirect all HTTP traffic to HTTPS.
#RewriteCond %{HTTPS} !=on
#RewriteRule ^/?(.*) https://%{SERVER_NAME}/$1 [R,L]
# Send / to /roundcube.
#RewriteRule ^/?$ /roundcube [L]
Edit the roudcube config/var/www/html/roundcube/config/config.inc.php to stop it from forcing ssl. Look for and change the line to false like below:
$config[‘force_https’] = false;
Remove https redirect from the default config in apache and remove the servername directive:
sudo vi /etc/apache2/sites-enabled/000-default.conf
#RewriteEngine on
#RewriteCond %{SERVER_NAME} =mail.warbel.net
#RewriteRule ^ https://%{SERVER_NAME}%{REQUEST_URI} [END,QSA,R=permanent]
#ServerName mail.warbel.net
This is important as we dont want incoming request to again be forwarded.
To fix forwarding/proxing issues with Owncloud there is ample documetion available on their site. The short of it is to edit /var/www/owncloud/config/config.php to include the following lines (modify to suit):
#information included to fix reverse proxying
#https://doc.owncloud.org/server/8.2/admin_manual/configuration_server/reverse_proxy_configuration.html
‘trusted_proxies’ => [‘0.0.0.0’],
‘overwritehost’ => ‘www.warbel.net’,
‘overwriteprotocol’ => ‘https’,
‘overwritewebroot’ => ‘/owncloud’,
‘overwritecondaddr’ => ‘^00\.0\.0\.0$’,
Then enable https rewriting in the /var/www/owncloud/.htaccess file. Owncloud is smart enough to know when its being accessed via proxy.
Change Edit: RewriteCond %{HTTPS} off
to RewriteCond %{HTTPS} on
Just to be safe, unload ssl and restart apache2.
sudo a2dismod ssl; sudo service apache2 restart
Test that ssl is disabled. I discovered that I needed to clear my cache/history, as Chrome would attempt to redirect to https as per my broswer history.
I have another server that handles Deluge and Sonar. I won’t go into depth here, but if you want those applications to be accessible via a reverse proxy then stop the programs and edit their configs. In Sonarr:
Edit the config for Sonarr, /home/<user>/.config/Nzbdrone/config.xml
Edit the line <UrlBase></UrlBase> to
<UrlBase>/sonarr</UrlBase>
In Deluge, edit the conf file: /home/<user>/.config/web.conf edit the line:
“base”: “/” to
“base”: “/deluge”
Start your services again and check they’re functional.
Now the fun part. (This should work, assuming you have letsencrypt already enabled). Enable the proxy modules in apache2:
sudo a2enmod proxy proxy_html proxy_connect; sudo service apache2 restart
Edit your main site’s ssl config in /etc/apache2/sites-enabled/sitename-ssl.config to include the following (again, edit to suit):
ProxyRequests Off
ProxyPreserveHost On
<Proxy *>
Order deny,allow
Allow from all
</Proxy>
ProxyPass /sonarr http://ipaddress:8989/sonarr
ProxyPassReverse /sonarr http://ipaddress:8989/sonarr
#Location directive included to stop unauthorised access to sonarr
<Location /sonarr>
AuthType Basic
AuthName “Sonarr System”
AuthBasicProvider file
AuthUserFile “/etc/apache2/htpasswd”
Require valid-user
</Location>
ProxyPass /deluge http://ipaddress:8112/
ProxyPassReverse /deluge http://ipaddress:8112/
ProxyPass /roundcube/ http://ipaddress/roundcube/
ProxyPassReverse /roundcube/ http://ipaddress/roundcube/
Redirect permanent /roundcube /roundcube/
ProxyPass /postfixadmin http://ipaddress/postfixadmin
ProxyPassReverse /postfixadmin http://ipaddress/postfixadmin
ProxyPass /owncloud/ http://ipaddress/owncloud/
ProxyPassReverse /owncloud/ http://ipaddress/owncloud/
Redirect permanent /owncloud /owncloud/index.php
A few notes on the directives:
- As Sonarr does not have authentication, I’ve used some resources to make it secure: If necessary, generate a strong random password for apache htaccess file here: http://passwordsgenerator.net/ And use this tool to create your htaccess file contents: http://www.htaccesstools.com/htpasswd-generator/
- The redirect permanent is useful is people try to access /roundcube, which won’t work, rather than /roundcube/ which will.
At this point you should be able restart everything and it will work (at least it did for me!). Please leave any questions or comments below.
Edit: You may want to stop people inside the network, depending on your dns etc requirements from accessing the mail server on port 80. If so, the following line in your firewall should do the trick, give or take:
$IPTABLES -A INPUT -p tcp –dport 80 ! -s ip.of.www.proxy -j DROP